Basic Pentesting
This Try Hack Me room guided users through the basics of web application pentesting. I learned about SMB enumeration and bruteforcing domains. This walkthrough also introduces bruteforcing logins with hydra and once the machine is compromised, elevating user privileges.
Tools #
- nmap
- gobuster
- hydra
- linenum
Walkthrough #
First things first let’s scan the box. I used the command nmap -sV -sS $IP and redirected the output to the file nmap/nmap.txt. It looks like there is an http server on this box. Let’s try and connect to it to see if it is actually accessible. Doesn’t look like we can access it. Let’s run a gobuster scan on the domain to just see if we can access any other pages. After running the command gobuster dir -u http://$IP:80 -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt, we can see that there is a directory called development. Let’s go to it in the browser and take a look.
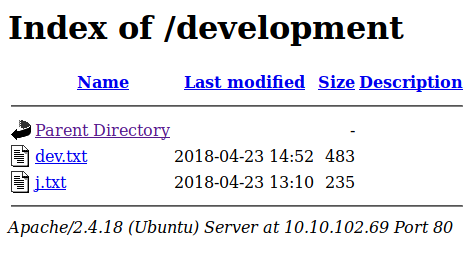
This is a great find because it indexes what we have in the directory. It looks like theses are internal notes.
2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat
to host that on this server too. Haven't made any real web apps yet, but I have tried that example
you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm
using version 2.5.12, because other versions were giving me trouble. -K
2018-04-22: SMB has been configured. -K
2018-04-21: I got Apache set up. Will put in our content later. -J
For J:
I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials,
and I was able to crack your hash really easily. You know our password policy, so please follow
it? Change that password ASAP.
-K
To sum up the notes, it sounds like the user J has a weak password. Our nmap scan showed that then ssh port was open we we might be able to try and brute force some credentials with hydra. After doing some research it looks like hydra might not be the first step. To figure out the users we need to enumerate the SMB port with the tool enum4linux. Use the command enum4linux -a $IP to enumerate the SMB configuration. I outputted this to a file called smb_enum.txt it found two users, jan and kay. Now that we have these usernames we can use hydra to bruteforce jan’s ssh password since we know she has a weak password. Use the command hydra -l jan -P /usr/share/wordlists/rockyou.txt $IP so start the attack. Once the attack has been completed we can see that jan’s password is armando.
username: jan
password: armando
Next I enumerated the possible exploits on our target machine. I used this article to learn how to use LinEnum to scan for vulnerabilities on the target machine. First I sshed into the machine then navigated to /var/tmp so that I could copy the LinEnum script onto the machine. Then I ran the script. It looks like kay might had misconfigured her ssh files. If we copy her private key and has it we should be able to find out her password with John. First exfiltrate the private key. Next, use the command python /usr/share/john/ssh2john.py id_rsa > id_rsa.hash. Now we can use JtR to break this hash against the RockYou wordlist. Use the command /usr/sbin/john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash against the has to crack it. And soon enough the password pops out as beeswax.
username: kay
password: beeswax
Now if we try to connect to the server with user kay we can use her passphase to use the private key. Use the command ssh -i id_rsa kay@$IP then enter beeswax when prompted for the private key password. If you get errors saying that the private key has bad permissions you can use the command chmod 600 id_rsa to fix that. Now we have access to the user kay. Cat out the password.bak file to get the final password and we are done! Congratulations!
After some more investigating, it also looks like we may even be able to become the root user from kay. If we run the command sudo -l and put in the password we just got we can see that kay can run sudo commands. So if we try to use the command sudo su we should be able to switch our user to root. And what do you know it works! There is also a flag in /root/flag.txt check it out.
